Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Se debe tener en cuenta: This feature may not be available in some browsers.
Estás usando un navegador obsoleto. No se pueden mostrar este u otros sitios web correctamente.
Se debe actualizar o usar un navegador alternativo.
Se debe actualizar o usar un navegador alternativo.
Seguridad informática
- Autor King Conan
- Fecha de inicio
Tim
Miembro habitual
- Mensajes
- 35.654
- Reacciones
- 27.684
Microsoft releases additional updates to protect against potential nation-state activity - Windows Experience Blog
June 2017 security update release
Microsoft Security Advisory 4025685
No será que no avisaron. A todas las empresas grandes nos avisaron personalmente del asunto hace un par de semanas o así.
June 2017 security update release
Microsoft Security Advisory 4025685
No será que no avisaron. A todas las empresas grandes nos avisaron personalmente del asunto hace un par de semanas o así.
Mondelez paralizada, no funciona ni la Web.
http://www.mondelezinternational.es/
Informan también que por lo de Maersk, el puerto de Rotterdam también está muy paradito.
http://www.elconfidencial.com/tecnologia/2017-06-27/ataque-ransomware-dla-piper-wannacry_1405839/
En España está afectando a los sistemas de algunas multinacionales como la ya citada Mondelez y los laboratorios Merck.
http://www.mondelezinternational.es/
Informan también que por lo de Maersk, el puerto de Rotterdam también está muy paradito.
http://www.elconfidencial.com/tecnologia/2017-06-27/ataque-ransomware-dla-piper-wannacry_1405839/
En España está afectando a los sistemas de algunas multinacionales como la ya citada Mondelez y los laboratorios Merck.
Tim
Miembro habitual
- Mensajes
- 35.654
- Reacciones
- 27.684
Durante las últimas horas se ha detectado un nuevo ransomware, todavía no se ha confirmado la tipología pero todo parece señalar hacia una nueva versión del malware Petya que en este caso utilizaría el exploit EternalBlue, que aprovecha una la vulnerabilidad en el protocolo SMB de Microsoft (CVE-2017-0144).
Después de cifrar los datos del equipo, se mostrará un mensaje como el siguiente y bloqueará el equipo:

En la muestra analizada se han detectado los siguientes indicadores de compromiso:
1.Borra el log de Windows utilizando Wevutil.
2.Configura una tarea para que se ejecute en un momento determinado.
3.Escribe en la partición principal del disco.
Se recomienda aplicar la siguiente actualización de Microsoft:
Microsoft Security Bulletin MS17-010 - Critical
Microsoft Security Bulletin MS17-010 - Critical
technet.microsoft.com
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an attacker ...
En caso de no poder parchear los sistemas, se recomienda deshabilitar SMBv1.
Actualizar y parchear WAF, navegadores y plugins.
Forzar la descarga de firmas del antivirus.
Notificar a los empleados que eviten abrir enlaces y documentos adjuntos de correos electrónicos que provengan de remitentes desconocidos.
Añadir los hashes que se han identificado en casos similares en los dispositivos que puedan bloquear los ficheros a través de este medio:
oMD5 Hash: 415FE69BF32634CA98FA07633F4118E1
oSHA-1 Hash: 101CC1CB56C407D5B9149F2C3B8523350D23BA84
oSHA-256 Hash: FE2E5D0543B4C8769E401EC216D78A5A3547DFD426FD47E097DF04A5F7D6D206
oMD5 Hash: 0487382A4DAF8EB9660F1C67E30F8B25
oSHA-1 Hash: 736752744122A0B5EE4B95DDAD634DD225DC0F73
oSHA-256 Hash: EE29B9C01318A1E23836B949942DB14D4811246FDAE2F41DF9F0DCD922C63BC6
oMD5 Hash: A1D5895F85751DFE67D19CCCB51B051A
oSHA-1 Hash: 101CC1CB56C407D5B9149F2C3B8523350D23BA84
oSHA-256 Hash: 17DACEDB6F0379A65160D73C0AE3AA1F03465AE75CB6AE754C7DCB3017AF1FBD
Estos hashes hacen referencia a los siguientes ficheros, relacionados con este ransomware:
oOrder-20062017.doc
omyguy.xls
oBCA9D6.exe
Restringir el acceso al puerto 80 de las siguientes direcciones IP:
84.200.16.242
111.90.139.247
Después de cifrar los datos del equipo, se mostrará un mensaje como el siguiente y bloqueará el equipo:
En la muestra analizada se han detectado los siguientes indicadores de compromiso:
1.Borra el log de Windows utilizando Wevutil.
2.Configura una tarea para que se ejecute en un momento determinado.
3.Escribe en la partición principal del disco.
Se recomienda aplicar la siguiente actualización de Microsoft:
Microsoft Security Bulletin MS17-010 - Critical
Microsoft Security Bulletin MS17-010 - Critical
technet.microsoft.com
This security update resolves vulnerabilities in Microsoft Windows. The most severe of the vulnerabilities could allow remote code execution if an attacker ...
En caso de no poder parchear los sistemas, se recomienda deshabilitar SMBv1.
Actualizar y parchear WAF, navegadores y plugins.
Forzar la descarga de firmas del antivirus.
Notificar a los empleados que eviten abrir enlaces y documentos adjuntos de correos electrónicos que provengan de remitentes desconocidos.
Añadir los hashes que se han identificado en casos similares en los dispositivos que puedan bloquear los ficheros a través de este medio:
oMD5 Hash: 415FE69BF32634CA98FA07633F4118E1
oSHA-1 Hash: 101CC1CB56C407D5B9149F2C3B8523350D23BA84
oSHA-256 Hash: FE2E5D0543B4C8769E401EC216D78A5A3547DFD426FD47E097DF04A5F7D6D206
oMD5 Hash: 0487382A4DAF8EB9660F1C67E30F8B25
oSHA-1 Hash: 736752744122A0B5EE4B95DDAD634DD225DC0F73
oSHA-256 Hash: EE29B9C01318A1E23836B949942DB14D4811246FDAE2F41DF9F0DCD922C63BC6
oMD5 Hash: A1D5895F85751DFE67D19CCCB51B051A
oSHA-1 Hash: 101CC1CB56C407D5B9149F2C3B8523350D23BA84
oSHA-256 Hash: 17DACEDB6F0379A65160D73C0AE3AA1F03465AE75CB6AE754C7DCB3017AF1FBD
Estos hashes hacen referencia a los siguientes ficheros, relacionados con este ransomware:
oOrder-20062017.doc
omyguy.xls
oBCA9D6.exe
Restringir el acceso al puerto 80 de las siguientes direcciones IP:
84.200.16.242
111.90.139.247
Discord Pie
iOS Developer
El que cae es porque quiere. :/
Pues si. Ya no hay virus como los de antes. Ahora le llaman virus a cualquier cosa
Discord Pie
iOS Developer
Hombre. Hoy día hay malwares mucho peores que los antiguos y lo peor es que ni te enteras que los tienes ni te puedes proteger.Pues si. Ya no hay virus como los de antes. Ahora le llaman virus a cualquier cosa
Pero en este caso no estamos ante uno de esos.
Discord Pie
iOS Developer
Apple Flies Top Brass into Australia to Lobby against Australia's Proposed Encryption Laws, not Negotiate
Me cago en la ignorancia del gobierno Australiano.
Me cago en la ignorancia del gobierno Australiano.

Discord Pie
iOS Developer
Una de las bulnerabilidades corregidas hoy en watchOS 3.2.3:
Wi-Fi
Available for: All Apple Watch models
Impact: An attacker within range may be able to execute arbitrary code on the Wi-Fi chip
Description: A memory corruption issue was addressed with improved memory handling.
CVE-2017-9417: Nitay Artenstein of Exodus Intelligence

https://nvd.nist.gov/vuln/detail/CVE-2017-9417
Current Description
Broadcom BCM43xx Wi-Fi chips allow remote attackers to execute arbitrary code via unspecified vectors, aka the "Broadpwn" issue.
Ya bautizado como "Broadpwn" afectaba por igual a macOS 10.12.5, iOS 10.3.2, watchOS 3.2.2 y tvOS 10.2.1.
La semana que viene Nitay Artenstein autor del descubrimiento va a dar una charla en la Black Hat sobre cómo puede ser usada la vulnerabilidad para tomar control del chip Wi-Fi y desde el mismo saltar a tomar control completo del dispositivo pudiendo ejecutar cualquier código en el procesador.
Black Hat USA 2017 | Briefings Schedule
In this talk, we'll take a deep dive into the internals of the BCM4354, 4358 and 4359 Wi-Fi chipsets, and explore the workings of the mysterious, closed-source HNDRTE operating system. Then, we'll plunge into the confusing universe of 802.11 standards in a quest to find promising attack surfaces.
Finally, we'll tell the story of how we found the bug and exploited it to achieve full code execution - and how we went on to leverage our control of the Wi-Fi chip in order to run code in the main application processor.
Actualizad ya insensatos...
Discord Pie
iOS Developer
La actualización de seguridad de Android de julio de 2017 también se encarga de arreglar este problema. De momento está disponible para los Pixel y Nexus: Pixel and Nexus devices get security update for July 2017 | TalkAndroid.com
Toda la info sobre la actualización de seguridad de julio:
Android Security Bulletin—July 2017 | Android Open Source Project
Toda la info sobre la actualización de seguridad de julio:
Android Security Bulletin—July 2017 | Android Open Source Project
Discord Pie
iOS Developer
Discord Pie
iOS Developer
Mac malware discovered in the wild allows webcam photos, screenshots, key-logging
[UPDATE: Apple confirmed to us that any systems that are up to date, running El Capitan or later, are protected. We’ve also confirmed from those in the know that the issue has been fixed since around January and only affected older and out of date Macs.]
[UPDATE: Apple confirmed to us that any systems that are up to date, running El Capitan or later, are protected. We’ve also confirmed from those in the know that the issue has been fixed since around January and only affected older and out of date Macs.]
Discord Pie
iOS Developer
- Mensajes
- 22.827
- Reacciones
- 7.375
Obsesionado no, estás neurótico perdío
Discord Pie
iOS Developer
I know
Discord Pie
iOS Developer
NVD - CVE-2017-9417
Current Description
Broadcom BCM43xx Wi-Fi chips allow remote attackers to execute arbitrary code via unspecified vectors, aka the "Broadpwn" issue.
Ya bautizado como "Broadpwn" afectaba por igual a macOS 10.12.5, iOS 10.3.2, watchOS 3.2.2 y tvOS 10.2.1.
La semana que viene Nitay Artenstein autor del descubrimiento va a dar una charla en la Black Hat sobre cómo puede ser usada la vulnerabilidad para tomar control del chip Wi-Fi y desde el mismo saltar a tomar control completo del dispositivo pudiendo ejecutar cualquier código en el procesador.
Black Hat USA 2017 | Briefings Schedule
In this talk, we'll take a deep dive into the internals of the BCM4354, 4358 and 4359 Wi-Fi chipsets, and explore the workings of the mysterious, closed-source HNDRTE operating system. Then, we'll plunge into the confusing universe of 802.11 standards in a quest to find promising attack surfaces.
Finally, we'll tell the story of how we found the bug and exploited it to achieve full code execution - and how we went on to leverage our control of the Wi-Fi chip in order to run code in the main application processor.
Actualizad ya insensatos...
Demo de este jueves en la Black Hat:
BROADPWN: REMOTELY COMPROMISING ANDROID AND IOS VIA A BUG IN BROADCOM’S WI-FI CHIPSETS
Nitay Artenstein dijo:[...]
THE BCM43XX FAMILY
Broadcom’s WiFi chips are the dominant choice for the WiFi slot in high-end smartphones. In a non-exhaustive research, we’ve found that the following models use Broadcom WiFi chips:
The chip model range from BCM4339 for the oldest phones (notably Nexus 5) up to BCM4361 for the Samsung Galaxy S8. This research was carried out on both a Samsung Galaxy S5 (BCM4354) and a Samsung Galaxy S7 (BCM4359), with the main exploit development process taking place on the S7.
- Samsung Galaxy from S3 through S8, inclusive
- All Samsung Notes3. Nexus 5, 6, 6X and 6P
- All iPhones after iPhone 5
[...]
All the BCM chips that we’ve observed run an ARM Cortex-R4 microcontroller. One of the system’s main quirks is that a large part of the code runs on the ROM, whose size is 900k. Patches, and additional functionality, are added to the RAM, also 900k in size. In order to facilitate patching, an extensive thunk table is used in RAM, and calls are made into that table at specific points during execution. Should a bug fix be issued, the thunk table could be changed to redirect to the newer code.
In terms of architecture, it would be correct to look at the BCM43xx as a WiFi SoC, since two different chips handle packet processing. While the main processor, the Cortex-R4, handles the MAC and MLME layers before handing the received packets to the Linux kernel, a separate chip, using a proprietary Broadcom processor architecture, handles the 802.11 PHY layer. Another component of the SoC is the interface to the application processor: Older BCM chips used the slower SDIO connection, while BCM4358 and above use PCIe.
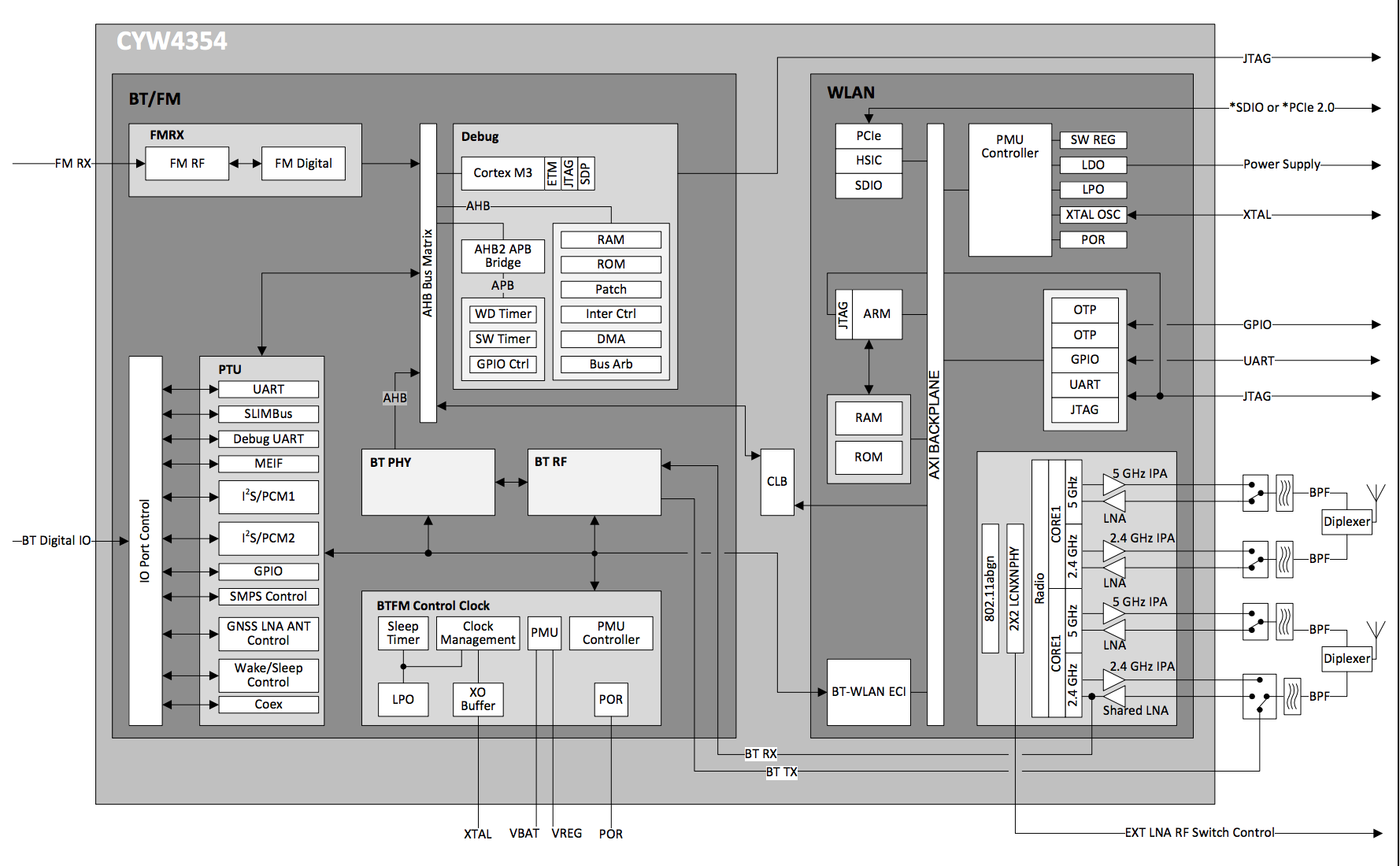
The main ARM microcontroller in the WiFi SoC runs a mysterious proprietary RTOS known as HNDRTE. While HNDRTE is closed-source, there are several convenient places to obtain older versions of the source code. Previous researchers have mentioned the Linux brcmsmac driver, a driver for SoftMAC WiFi chips which handle only the PHY layer while letting the kernel do the rest. While this driver does contain source code which is also common to HNDRTE itself, we found that that most of the driver code which handles packet processing (and that’s where we intended to find bugs) was significantly different to the one found in the firmware, and therefore did not help us with reversing the interesting code areas.
The most convenient resource we found was the source code for the VMG-1312, a forgotten router which also uses a Broadcom chipset. While the brcmsmac driver contains code which was open-sourced by Broadcom for use with Linux, the VMG-1312 contains proprietary Broadcom closed-source code, bearing the warning “This is UNPUBLISHED PROPRIETARY SOURCE CODE of Broadcom Corporation”. Apparently, the Broadcom code was published by mistake together with the rest of the VMG-1312 sources.
The leaked code contains most of the key functions we find in the firmware blob, but it appears to be dated, and does not contain much of the processing code for the newer 802.11 protocols. Yet it was extremely useful during the course of this research, since the main packet handling functions have not changed much. By comparing the source code with the firmware, we were able to get a quick high-level view of the packet processing code section, which enabled us to hone in on interesting code areas and focus on the next stage: finding a suitable bug.
[...]
References
[a] While KASLR is still largely unsupported on Android devices, the large variety of kernels out there effectively means that an attacker can make very few assumptions about an Android kernel’s address space. Another problem is that any misstep during an exploit will cause a kernel panic, crashing the device and drawing the attention of the victim.
The BCM43xx family has been the subject of extensive security research in the past. Notable research includes Wardriving from Your Pocket (https://recon.cx/2013/slides/Recon2013-Omri Ildis, Yuval Ofir and Ruby Feinstein-Wardriving from your pocket.pdf) by Omri Ildis, Yuval Ofir and Ruby Feinstein; One Firmware to Monitor ’em All (http://archive.hack.lu/2012/Hacklu-2012-one-firmware-Andres-Blanco-Matias-Eissler.pdf) by Andres Blanco and Matias Eissler; and the Nexmon project by SEEMOO Lab (GitHub - seemoo-lab/nexmon: The C-based Firmware Patching Framework for Broadcom/Cypress WiFi Chips that enables Monitor Mode, Frame Injection and much more ). These projects aimed mostly to implement monitor mode on Nexus phones by modifying the BCM firmware, and their insights greatly assisted the author with the current research. More recently, Gal Beniamini of Project Zero has published the first security-focused report about the BCM43xx family (https://googleprojectzero.blogspot.ca/2017/04/over-air-exploiting-broadcoms-wi-fi_4.html), and has discovered several bugs in the BCM firmware.
This function does not exist in the source code that we managed to obtain, so the naming is arbitrary.
[d] Gal Beniamini’s second blog post about BCM deals extensively with this issue (Project Zero: Over The Air: Exploiting Broadcom’s Wi-Fi Stack (Part 2) ). And while a kernel read primitive is not demonstrated in that post, the nature of the MSGBUF protocol seems to make it possible.
[e] This is an estimate, and was determined by looking up the OUI part of the sniffed device’s MAC address.
A parte de vuestros móviles, tablets, relojes, ordenadores etc. no olvidéis revisar vuestros puntos de acceso inalámbricos. Os recomiendo estas dos wikis para ver que chips utilizan vuestros cacharros:
- para puntos de acceso y routers: OpenWrt
- para todos los dispositivos: WikiDevi
- para ver información extra sobre los distintos modelos de SoC de Broadcom: Broadcom Limited | Connecting Everything
Última edición:
Hinomura Krycek
Bayofilo
Tu tienes algo que ocultar?
Discord Pie
iOS Developer
Hinomura Krycek
Bayofilo
No has respondido a mi pregunta.
Algo ocultas.
Algo ocultas.


